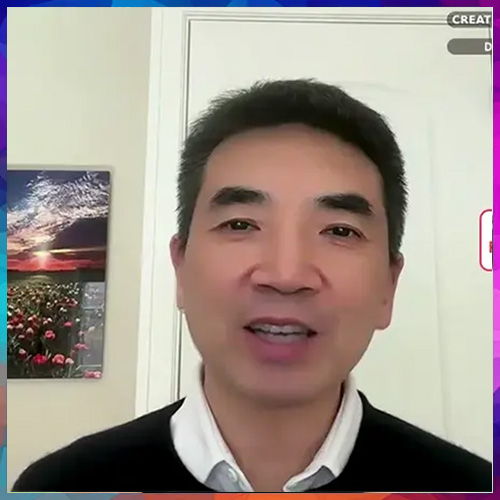
Zoom’s latest use of an AI avatar by CEO Eric Yuan, together with the corporate’s plan to introduce customized AI avatars in early 2025, underscores how quickly artificial media is changing into a part of on a regular basis enterprise communication.
To construct confidence, Zoom shows a visual watermark—“Created with Zoom AI Companion.” Whereas the intent is transparency, the strategy dangers changing into safety risk fairly than providing significant safety.
The basic flaw is that visible indicators are inherently straightforward to copy.
An attacker can reproduce the identical badge, font, and placement in seconds.
Even when Zoom implements robust backend protections resembling cryptographic signing, metadata verification, or audit trails, most customers won’t ever validate them.
As an alternative, they depend on what they see.
Over time, the watermark shifts from being a disclosure mechanism to a perceived authentication sign—and that misplaced belief is precisely what attackers exploit.
This creates specific threat in hierarchical organizations.
Workers are sometimes reluctant to problem requests that seem to return from senior management.
When an “official-looking” badge is current, skepticism drops even additional.
The Arup deepfake fraud incident, the place employees transferred thousands and thousands after a faux govt video name, highlights how organizational dynamics can overpower technical safeguards.
As AI avatars turn into normalized, suspicion naturally declines, assault surfaces broaden, and accountability turns into more durable to find out.
The true hazard lies not in avatar know-how itself, however within the false sense of safety it creates.
To counter this, organizations should deal with video-based communications as low-trust by default, implement secondary verification for delicate actions, and clearly practice staff that watermarks sign disclosure—not authenticity.
Leave a Reply